Math 152 - Intro to Mathematical Software
2017-03-13
Kiran Kedlaya; University of California, San Diego
adapted from lectures by William Stein, University of Washington
Guest lecturer (and worksheet author): Kartik Venkatram
** Lecture 26: Public key cryptography and number theory, part 1 **
Announcements:
Kiran will be monitoring the chat room this hour.
No sections today.
Additional guest lecture Wednesday: Alina Bucur
Office hours this week:
Zonglin: Thursday, March 16, 3:30-5:30 in APM 5748.
Kiran: Friday, March 17, 11-12 in APM 7202.
Peter: Friday, March 17, 12-1 and 3-4 in APM 6132.
Homework due Friday, 8pm. Peer grading due Sunday, 8pm.
No final exam!
Please do your course evaluation (CAPE)! Evaluations close Monday, March 20 at 8am.

Finite Field of size 23
13+17 = 7
13*17 = 14
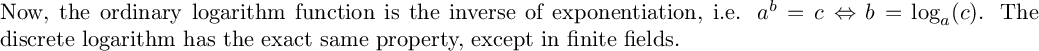
13 ^ 5 = 4
log_ 13 4 = 5
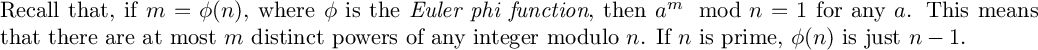
phi(p) = 22
powers of 5: [1, 5, 2, 10, 4, 20, 8, 17, 16, 11, 9, 22, 18, 21, 13, 19, 3, 15, 6, 7, 12, 14, 1, 5, 2, 10, 4, 20, 8, 17, 16, 11, 9, 22, 18, 21, 13, 19, 3, 15, 6, 7, 12, 14]
powers of 2: [1, 2, 4, 8, 16, 9, 18, 13, 3, 6, 12, 1, 2, 4, 8, 16, 9, 18, 13, 3, 6, 12, 1, 2, 4, 8, 16, 9, 18, 13, 3, 6, 12, 1, 2, 4, 8, 16, 9, 18, 13, 3, 6, 12]

625 loops, best of 3: 98.2 µs per loop
5 loops, best of 3: 137 ms per loop


425438 425438
CPU time: 0.18 s, Wall time: 0.19 s

3059695168 3059695168
CPU time: 0.21 s, Wall time: 0.20 s
p = 18446739937656050359
p-1 = 2 * 3^2 * 13^2 * 1411889 * 4294967291
4541974040081333206 4541974040081333206
CPU time: 0.54 s, Wall time: 0.53 s
